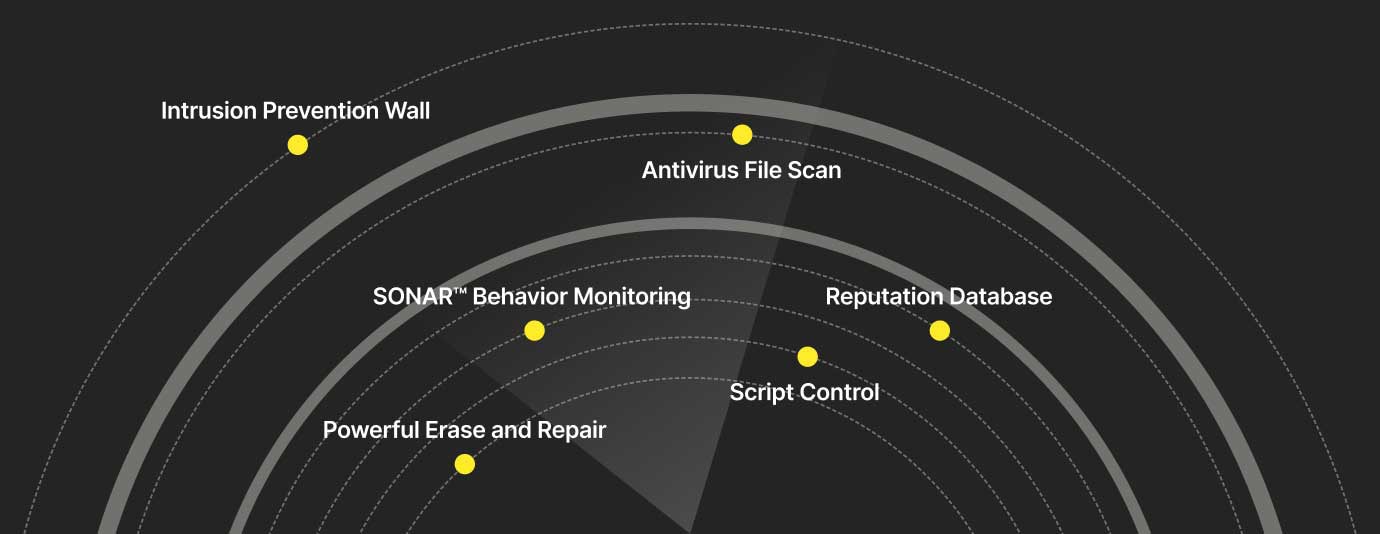
As a key component in cybersecurity solutions, firewalls help protect your devices specifically by doing the following:
- Helping preventing access by unauthorized users through the Internet
- Monitoring communication between your computer and other computers on the Internet
- Providing a filter that allows or blocks attempts to access the information on your computer, based on pre-set rules
- Warning you if another computer attempts to connect to yours
- Warning you if the applications on your computer attempt to connect to other computers
Firewalls are one component of protection for your computer. Cybersecurity solutions include several more key technological components that work together to help protect your devices in different ways, such as antivirus technology that works to help protect your information at the file level. Just as you would if you want to protect your home with security cameras and motion sensors, strong locks on the doors and windows, and a guard dog who barks stridently whenever someone approaches, cybersecurity solutions use multiple means for protection, including a firewall that is designed to protect against unauthorized access, and from the wrong data getting in or out of your computer.